Bathroom Hand Held Spa Shower Head Round Nozzle Ultra thin Boost Chrome Shower Head Bathroom Shower Accessories|Shower Heads| - AliExpress

What is a side channel attack? How these end-runs around encryption put everyone at risk | CSO Online

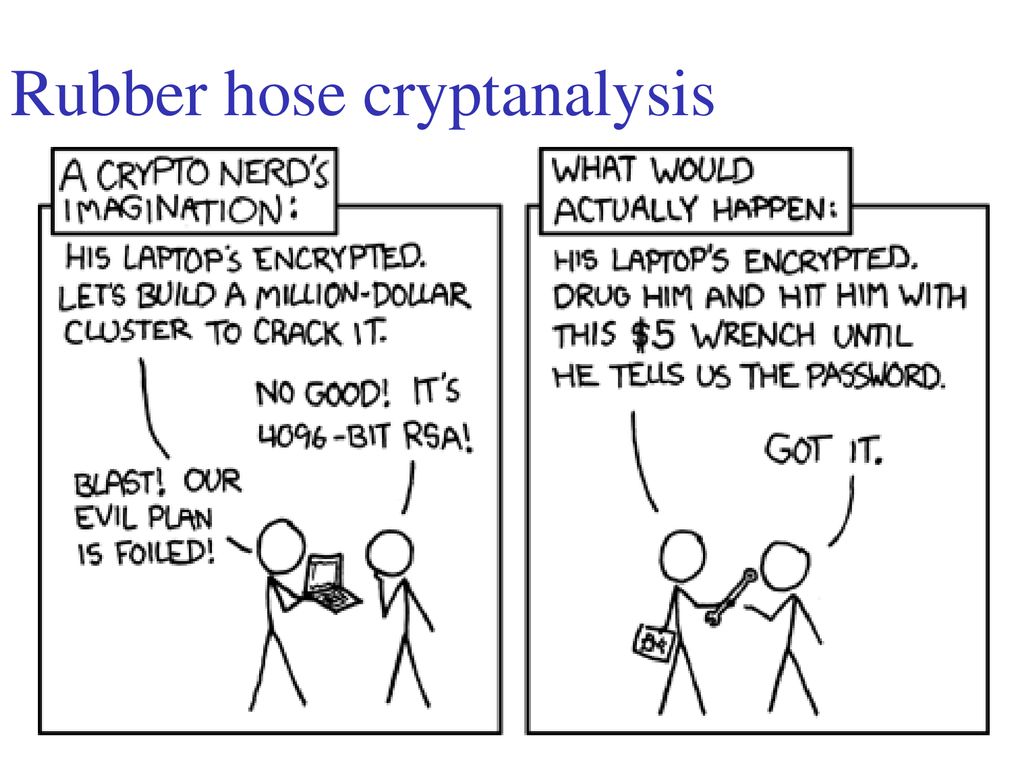
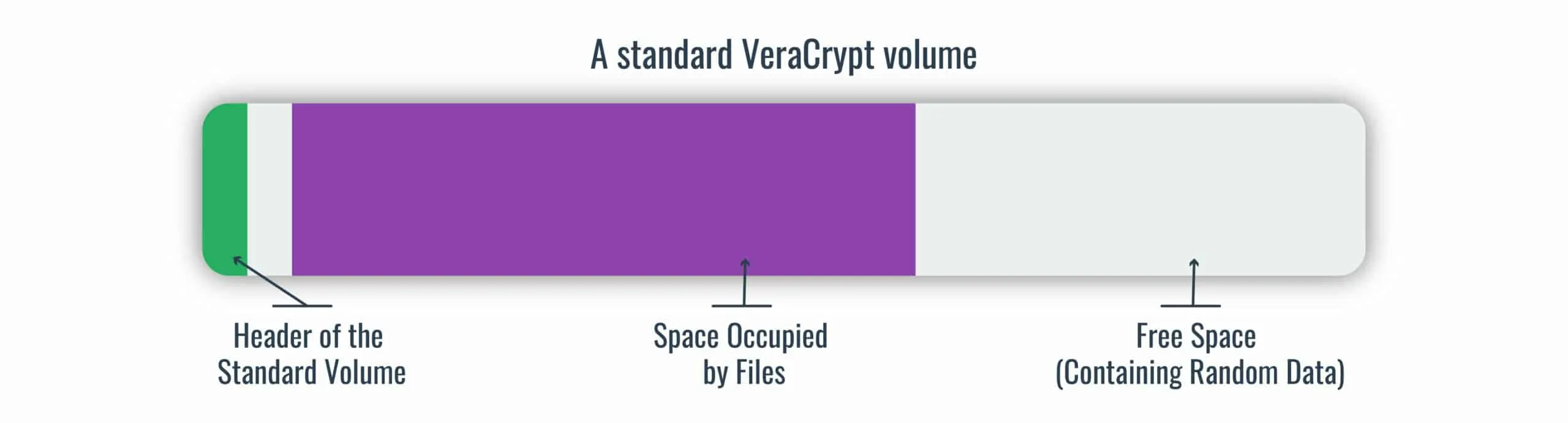
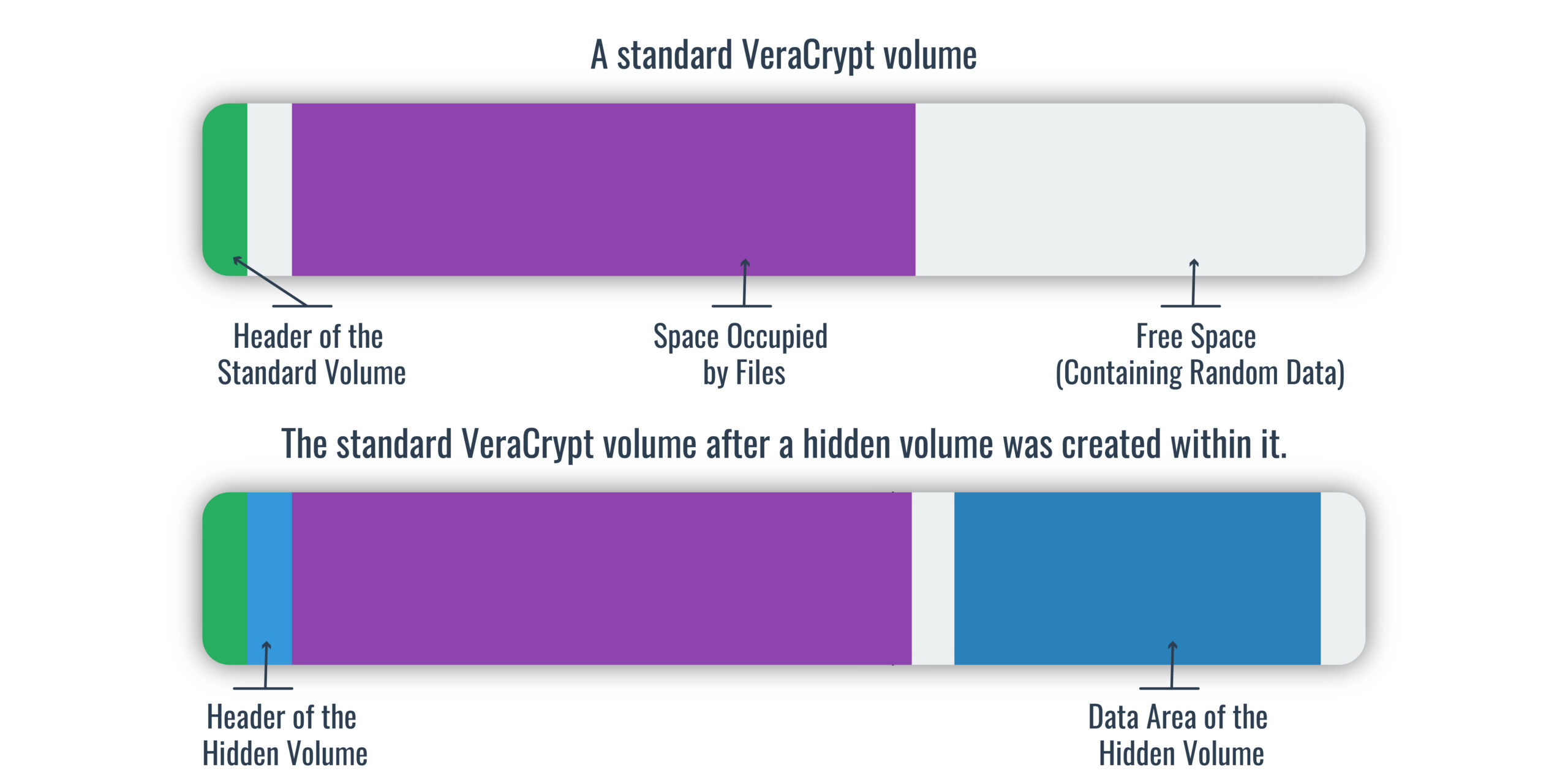
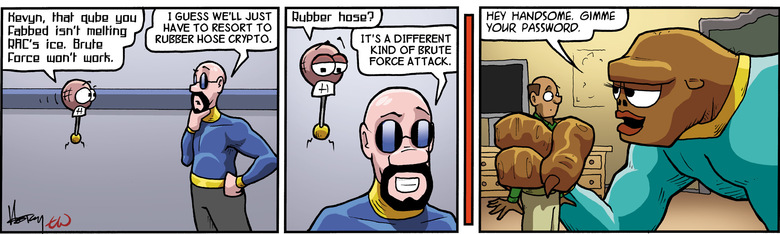
Anonymous Ghostwriters - Rubber Hose Cryptography works by filling the entire hard drive with random characters that are indistinguishable from encrypted data. The file system then takes each archive of real data
GitHub - Cookie04DE/Sekura: Encryption tool that's heavily inspired by the Rubberhose file system (https://en.wikipedia.org/wiki/Rubberhose _(file_system)).
Can't send PGP message that is encrypted, but not signed, since 5.200 · Issue #1961 · thundernest/k-9 · GitHub