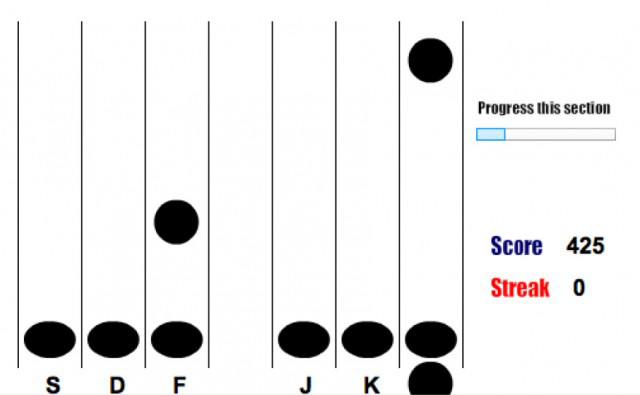
Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks A Paper by Hristo Bojinov, Daniel Sanchez, Paul Reber, - ppt download

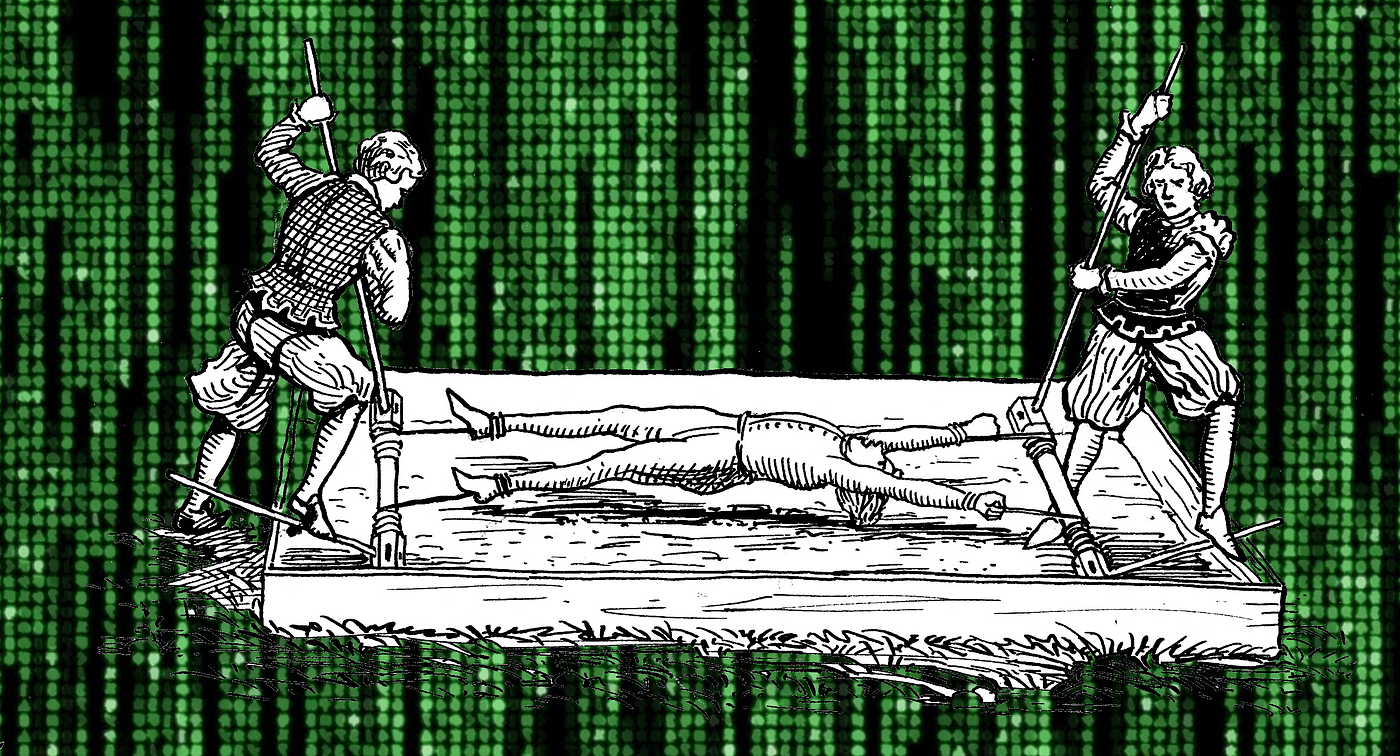
Amazon.it: Side-Channel Attack: Cryptography, Cryptosystem, Brute Force Attack, Electromagnetic Radiation, Key (Cryptography), History of Cryptography, Cryptanalysis, Rubber-Hose Cryptanalysis - Surhone, Lambert M., Timpledon, Miriam T., Marseken ...

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks | USENIX
Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks - YouTube

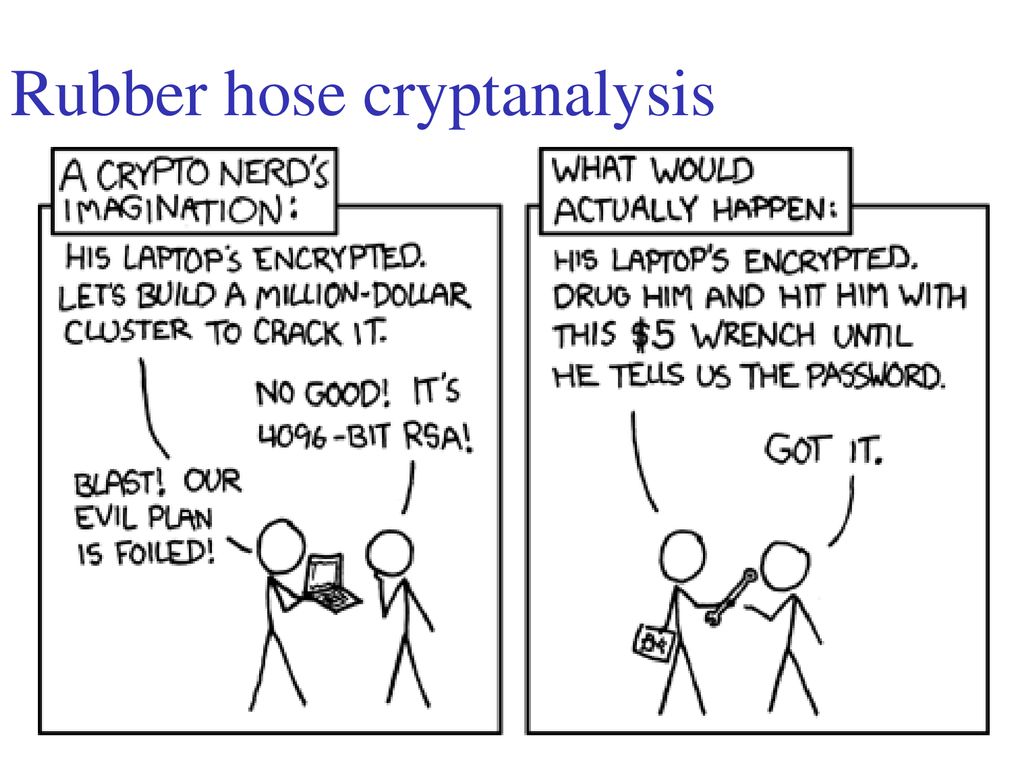
Programmer Humor on Twitter: "Cryptography: expectations vs. reality https://t.co/RD8Tfg057p https://t.co/IpB6X3VFtz" / Twitter

Amazon.co.jp: Rubber-Hose Cryptanalysis : Surhone, Lambert M., Timpledon, Miriam T., Marseken, Susan F.: Japanese Books

Amazon.co.jp: Rubber-Hose Cryptanalysis : Surhone, Lambert M., Timpledon, Miriam T., Marseken, Susan F.: Japanese Books